Official 2014 Latest Microsoft 70-410 Exam Dump Free Download(321-330)!
QUESTION 321
You have a server named Server1 that runs Windows Server 2012 R2. On Server1, you open Computer Management as shown in the exhibit. (Click the Exhibit button.)
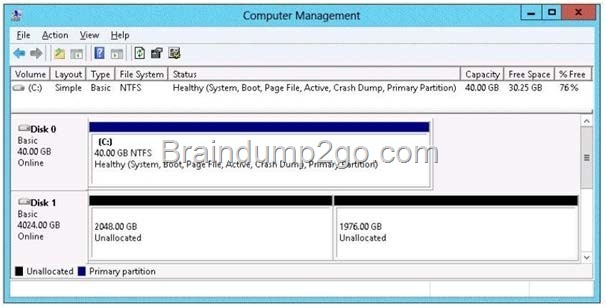
You need to ensure that you can create a 3-TB volume on Disk 1. What should you do first?
A. Create a storage pool.
B. Convert the disk to a GPT disk.
C. Create a VHD, and then attach the VHD.
D. Convert the disk to a dynamic disk.
QUESTION 322
You have 3 server named Server1. Server1 runs a Server Core installation of Windows Server 2012 R2. The local area connection on Server1 has the following configuration:
IP address: 10.1.1.1
– Subnet mask: 255.255.240.0
– Default gateway: 10.1.1.254
– Preferred DNS server: <none>
The network contains a DNS server that has an IPv4 address of 10.1.1.200. You need to configure Server1 to use 10.1.1.200 as the preferred DNS server. The solution must not change any other settings on Server1.
Which command should you run?
A. sconfig.cmd
B. net.exe
C. Set-NetIPInterface
D. netsh.exe
Answer: A
Explanation:
In Windows Server 2012 R2, you can use the Server Configuration tool (Sconfig.cmd) to configure and manage several common aspects of Server Core installations. Network settings You can configure the IP address to be assigned automatically by a DHCP Server or you can assign a static IP address manually. This option allows you to configure DNS Server settings for the server as well.
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image0016_thumb.jpg)
Sconfig.cmd interface
QUESTION 323
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a domain controller, named L2P-DC01. You have been instructed to make sure that the Group Policy Administrative Templates are available centrally.
Which of the following actions should you take?
A. You should consider copying the policies folder to the PolicyDefinitions folder in the L2P.com
domain’s SYSVOL folder.
B. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s SYSVOL folder.
C. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s systemroot folder.
D. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s logonserver folder.
Answer: B
Explanation:
PolicyDefinitions folder within the SYSVOL folder hierarchy. By placing the ADMX files in this directory, they are replicated to every DC in the domain; by extension, the ADMX-aware Group Policy Management Console in Windows Vista, Windows 7, Windows Server 2008 and R2 can check this folder as an additional source of ADMX files, and will report them accordingly when setting your policies.
By default, the folder is not created. Whether you are a single DC or several thousand, I would strongly recommend you create a Central Store and start using it for all your ADMX file storage. It really does work well.
The Central Store To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in the following location: \\FQDN\SYSVOL\FQDN\policies
Note: FQDN is a fully qualified domain name.
http://tigermatt.wordpress.com/tag/policydefinitions/
http://support.microsoft.com/kb/929841/en-us
http://www.virtuallyimpossible.co.uk/how-to-create-a-group-policy-central-store/ http://support.microsoft.com/kb/2741591/en-us
QUESTION 324
Your network contains an Active Directory domain named contoso.com. The password policy for the domain is set to require a minimum password length of 10 characters. A user named User1 and a user named User2 work for the sales department. User1 is forced to create a domain password that has a minimum of 12 characters. User2 is forced to create a domain password that has a minimum of eight characters. You need to identify what forces the two users to have different password lengths.
Which tool should you use?
A. Credential Manager
B. Security Configuration Wizard (SCW)
C. Group Policy Management
D. Active Directory Administrative Center
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc770842(v=ws.10).aspx
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain. For example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and then apply less strict settings to the accounts of other users. Or in some cases, you may want to apply a special password policy for accounts whose passwords are synchronized with other data sources.
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image00110_thumb.jpg)
QUESTION 325
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a Hyper-V server, named L2P-SR13, which hosts multiple virtual machines.
You have enabled the use of Single-root I/O virtualization.
Which of the following is TRUE with regards to using Single-root I/O virtualization? (Choose all that apply.)
A. It maximizes network throughput, while minimizing network latency.
B. It maximizes network throughput, as well as network latency.
C. It avoids the virtual switch stack and allows the virtual machine direct access to the actual network switch.
D. It prevents the virtual machine from accessing the network switch directly.
Answer: AC
Explanation:
SR-IOV enables network traffic to bypass the software switch layer of the Hyper-V
virtualizationstack. Because the VF is assigned to a child partition, the network traffic flows directly between the VF and child partition. As a result, the I/O overhead in the software emulation layer is diminished and achieves network performance that is nearly the same performance as in nonvirtualized environments.
http://msdn.microsoft.com/en-us/library/windows/hardware/hh440148%28v=vs.85%29.aspx
QUESTION 326
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators. You are currently discussing the use of Non-Uniform Memory Architecture (NUMA).
Which of the following is TRUE with regards to Non-Uniform Memory Architecture (NUMA)? (Choose two.)
A. It is a computer architecture used in multiprocessor systems.
B. It is a computer architecture used in single processor systems.
C. It allows a processor to access local memory faster than it can access remote memory.
D. It allows a processor to access remote memory faster than it can access local memory.
Answer: AC
Explanation:
NUMA is a hardware design feature that divides CPUs and memory in a physical server into NUMA nodes. You get the best performance when a process uses memory and CPU from within the same NUMA node.
de is full, then it’ll get memory from
When a process requires more memory, but the current NUMA no
another NUMA node and that comes at a performance cost to that process, and possibly all other processes on that physical server.
And that’s why virtualization engineers need to be aware of this. In Hyper-V we have Dynamic Memory.
Non-Uniform Memory Access or Non-Uniform Memory Architecture (NUMA) is a computer memory design used in multiprocessors, where the memory access time depends on the memory location relative to a processor. Under ccNUMA, a processor can access its own local memory faster than non-local memory, that is, memory local to another processor or memory shared between processors. NUMA architectures logically follow in scaling from symmetric multiprocessing (SMP) architectures.
http://en.wikipedia.org/wiki/Non-Uniform_Memory_Access
http://www.aidanfinn.com/?p=11945
QUESTION 327
Hotspot Question
You have a server named DHCP1 that runs Windows Server 2012 R2. DHCP1 does not ave access to the Internet. All roles are removed completely from DHCP1. You mount a Windows Server 2012 R2 installation image to the C:\Mount folder. You need to install the DHCP Server server role on DHCP1 by using Server Manager. Which folder should you specify as the alternate path for the source files?To answer, select the appropriate folder in the answer area.
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image00112_thumb.jpg)
Answer:
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image00114_thumb.jpg)
QUESTION 328
You have a server named Data1 that runs a Server Core Installation of Windows Server 2012 R2 Standard. You need to configure Data1 to run a Server Core Installation of Windows Server 2012 R2 Enterprise. You want to achieve this goal by using the minimum amount of administrative effort.
What should you perform?
A. a clean installation of Windows Server 2012
B. an offline servicing by using Dism
C. an online servicing by using Dism
D. an upgrade installation of Windows Server 2012
Answer: C
Explanation:
ROD: windows server 2012 enterprise DOES NOT EXIST, maybe they meant data center?
http://technet.microsoft.com/en-us/library/hh825157.aspx
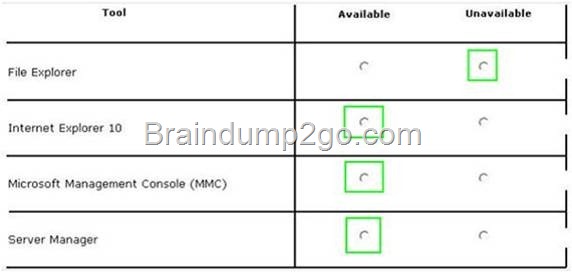
QUESTION 329
You have a server named Server1 that runs Windows Server 2012 R2. You need to enable access-based enumeration for a file share on Server1. Which tool should you use?
A. File Server Resource Manager (FSRM)
B. File Explorer
C. Share and Storage Management
D. Server Manager
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/dd772681(v=WS.10).aspx
Access-based enumeration displays only the files and folders that a user has permissions to access. It is a feature that was previously available as a downloadable package for the Windows Server® 2003 operating system (it was also included in Windows Server 2003 Service Pack 1). Access-based enumeration is now included in the Windows Server 2008 operating system, and you can enable it by using Share and Storage Management.
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image00116_thumb.jpg)
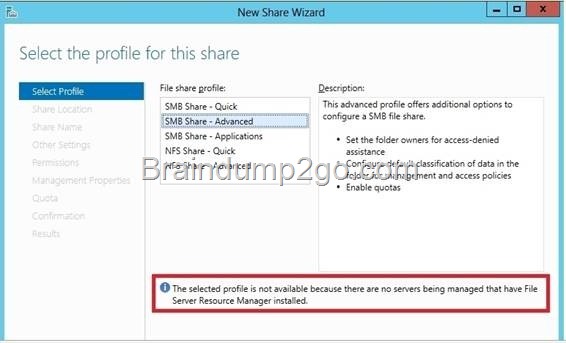
QUESTION 330
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2. You plan to create a shared folder. The shared folder will have a quota limit. You discover that when you run the New Share Wizard, you cannot select the SMB Share – Advanced option. You need to ensure that you can use SMB Share – Advanced to create the new share. What should you do on Server1 before you run the New Share Wizard?
A. Run the Set-SmbSharecmdlet.
B. Install the File Server Resource Manager role service.
C. Configure Dynamic Access Control and App1y a central access policy.
D. Configure the Advanced system settings.
Passing Microsoft 70-410 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-410 Dump:
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/c1b383968a34_9ACE/clip_image0014_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00144_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00224_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00146_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00148_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00152_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00226_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00156_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00228_thumb.jpg)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00158_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00234_thumb.jpg)
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00160_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00236_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00132_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00138_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00140_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00222_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00212_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00214_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00114_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00218_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00220_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image00116_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0014_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0024_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0016_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0026_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0018_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0028_thumb_3.jpg)
![clip_image001[55] clip_image001[55]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00155_thumb.jpg)
![clip_image001[57] clip_image001[57]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00157_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00232_thumb.jpg)
![clip_image001[59] clip_image001[59]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00159_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00236_thumb.jpg)
![clip_image001[61] clip_image001[61]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00161_thumb.jpg)
![clip_image001[63] clip_image001[63]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00163_thumb.jpg)
![clip_image001[33] clip_image001[33]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00133_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00218_thumb.jpg)
![clip_image001[35] clip_image001[35]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00135_thumb.jpg)
![clip_image001[37] clip_image001[37]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00137_thumb.jpg)
![clip_image001[39] clip_image001[39]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00139_thumb.jpg)
![clip_image001[41] clip_image001[41]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00141_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00226_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00228_thumb.jpg)
![clip_image001[43] clip_image001[43]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00143_thumb.jpg)
![clip_image001[45] clip_image001[45]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00145_thumb.jpg)
![clip_image001[47] clip_image001[47]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00147_thumb.jpg)
![clip_image001[49] clip_image001[49]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00149_thumb.jpg)
![clip_image001[51] clip_image001[51]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00151_thumb.jpg)
![clip_image001[53] clip_image001[53]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00153_thumb.jpg)
![clip_image001[25] clip_image001[25]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00125_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00212_thumb.jpg)
![clip_image001[27] clip_image001[27]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00127_thumb.jpg)
![clip_image001[29] clip_image001[29]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00129_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00214_thumb.jpg)
![clip_image001[31] clip_image001[31]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00131_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00216_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00114_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0026_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00118_thumb.jpg)
![clip_image001[21] clip_image001[21]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00121_thumb.jpg)
![clip_image001[23] clip_image001[23]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00123_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00210_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00110_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0024_thumb.jpg)